Computer Security
last update: 9 February 2022
These webpages are a collection of computer security information, articles, etc., from the very practical to the academic.
Topics I've looked at so far are:-
2020
Homeland Threat Assessment 2020.
Key Computer Security Topics in 2020
2020 came with a whole new level of cybersecurity threats, ones that was increasingly difficult to summarise on one page. Firstly, companies faced an increase in premeditated, well planned internet outages, and cloud vulnerability continued to be one of the biggest cybersecurity challenges. Forbes predicted that 83% of enterprise workload will have moved to the cloud by 2020. They are tempting targets for malicious hackers. Data breach, misconfiguration, insecure interfaces and APIs, account hijacking (e.g. Twitter), malicious insider threats, and DDoS attacks are among the top cloud security threats that will continue to pose problems. Security misconfiguration, intentional or otherwise, can start with poorly configured permissions and access controls to cloud services, and end with a total data breach such the Nintendo data leak and the CAM4 exposure of 10 billion records. Despite dating from 2017 Operation Cloud Hopper by Red Apollo also makes for an interesting read.
Early in 2020, due to the COVID-19 pandemic, most businesses across the globe found they needed to shift quickly to remote work, some did so according to a plan, others reacted but not according to their plan, and still more did not even have a plan. Remote work challenged enterprise security monitoring in numerous ways from the platforms used for communication to the devices people are using and networks on which they transmit data. There was an increase in social engineering opportunities as cyberespionage and cybercriminal groups attempted to take advantage of vulnerable employees unfamiliar with managing their technology environments.
Health advisory information on COVID was used to introduce malicious documents, e.g. ROHU, Snakeflounder, Needlefish, Stickleback, etc. (see this report).
The virus panic served as merely the latest tool in ongoing attempts to spy on, discredit and weaken adversary governments. In addition to the financially motivated COVID-19-themed phishing activity, COVID-19 related lure documents dropped cyberespionage malware linked to several nation-state groups. They looked to breached healthcare services looking for intelligence on pandemic-related topics, such as disease spread or vaccine and pharmaceutical research.
Governments and private sector entities tracked COVID-19 infections and promoted social distancing to slow the disease’s spread. In at least one case, a major online app store removed a COVID-19 health-tracking app after determining that a government was secretly collecting data on its own citizens with help from the app. In South Korea, government agencies used surveillance-camera footage, smartphone location data and credit card purchase records to help trace the recent movements of coronavirus patients and establish virus transmission chains. In Lombardy, Italy, the authorities analysed location data transmitted by citizens’ mobile phones to determine how many people were obeying a government lockdown order and the typical distances they move every day. They found that about 40 percent were moving around "too much". In Israel, the country’s internal security agency started using a cache of mobile phone location data, originally intended for counterterrorism operations, to try to pinpoint citizens who may have been exposed to the virus.
Alongside finding new ways to infect businesses with ransomware, threat actors found new ways to influence victims to pay. In November 2019, a new, game-changing strain of ransomware known as Maze infected a large security staffing company. Company data was stolen, the media notified, and eventually 700MB of data was publicly released when the ransom was not paid. This "name and shame" approach adds pressure on victims to pay up, even though law enforcement and the cybersecurity industry have always advised against paying ransoms. The situation could become far worse. As threat actor profits increase, they can innovate and invest in more advanced ransomware, and take advantage of the greater vulnerabilities of remote working.
The Maze and DoppelPaymer ransomware groups promised to spare hospitals, but then Maze released information stolen from a medical research company. While most ransomware serves as a money-maker for cybercriminals, politically motivated cyberthreat actors increasingly use ransomware, DDoS and other disruptive operations to weaken and discredit adversary governments.
One government noted that approximately one quarter of cyber incidents were associated with attacks on critical infrastructure or essential services, in particular health care, food distribution and energy sectors.
In a past survey, 88% of Americans stated to be greatly or somewhat confused about basic facts due to fake news. Ofcom, the UK’s media regulator, issued a report stating that half of UK adults receive news through social media sites, with 75% of these stating this includes Facebook as a source. This is despite the fact that social media were not rated as impartial, trustworthy or accurate (even as compared to TV). There are different types of fake news. e.g. for profit, for political gain, for crime, hoaxes, and viral pranks. Increasingly fake news has hybrid objectives, e.g. creating a hoax that puts a political candidate in a bad light may create political gain, and with the "right" advertising being displayed around the fake news story it may also generate a nice profit. If the creators of such a campaign could be identified they are likely to have committed a crime, but identifying the source is not always possible.
The weaponisation of information, be it disinformation or propaganda, is set to continue as the benefactors explore and adopt new methods to attack democracy or to make money. At the centre is data mining, and the ability to adjust and manipulate (i.e. customise) the message sent to an individual.
Deepfakes are increasing in quality at an impressive rate, and videos abound where someone is made to say something that is exactly opposite to what they think. Morphing effortlessly between different faces highlights the huge problem of detecting deepfakes. Are we ready for the real impact of deepfakes? With political scandals, pseudonudes and almost unimaginable scenarios involving fake videos, we may be staring blankly at the beginning of a new form of epidemic where the line between truth and lie may be impossible to determine. At the other and of the spectrum, completely new films can be made with actors that are long dead. Those actors will become no different from Donald Duck to Mickey Mouse.
Facial recognition is becoming more prevalent, while also attracting some negative press. Some US cities banned facial recognition being used by law enforcement after it wrongly identified 26 people as criminals who were law-abiding citizens. In fact, research by the US Government Accountability Office found that FBI algorithms were inaccurate 14% of the time, as well as being more likely to misidentify people of colour and women. Furthermore, Microsoft refused to install facial recognition technology for a US police force, due to concerns about machine-learning bias. This is where data have been input by humans, who tend to have various unintentional biases that influence the machine-learning outcome.
Continuing on the topic of machine learning, two new threats have been mentioned. Firstly, "AI Fuzzing" which integrates AI with traditional fuzzing techniques to create a tool that detects system vulnerabilities. AI fuzzing can help enterprises detect and fix the exploitable vulnerabilities in their system, it can also be used by cybercriminals to start, automate, and accelerate zero-day attacks. Secondly, Machine Learning Poisoning, where the target is to corrupt the machine learning model making it vulnerable to attacks. Machine learning models typically use data that is crowd-sourced or taken from social media. They also exploit user-generated information such as satisfaction ratings, purchasing histories, or web traffic. Cybercriminals engaging in "poisoning" could potentially use malicious samples or introduce backdoors or Trojans to poison training sets and compromise the systems.
In many countries there had been a substantial increase in skimming devices used on ATM machines, stealing user’s information, resulting in a substantial increase in fraudulent transactions. And increase of 148% from 2019 to 2020 was mentioned. Global losses for 2020 were estimated at $32.39 billion.
State sponsored attacks in 2020. There is a massively long list available here covering 2006-2022.
January 2020 started with different groups of hackers attacked the UN systems in Europe, two US municipalities, a Ukrainian energy company, mobile phones of two dozen Pakistani government officials, the Austrian foreign ministry and the Albanian state intelligence. It was claimed that state-backed hackers working to advance Turkish interests attacked at least 30 organisations, including government ministries, embassies and security services as well as companies and other groups. It included Cypriot and Greek government email services and the Iraqi government’s national security advisor. The hackers used a technique known as DNS hijacking, which involves tampering with the address book of the internet, called the Domain Name System (DNS), which enables computers to match website addresses with the correct server. By reconfiguring parts of this system, hackers were able to redirect visitors to imposter websites, such as a fake email service, and capture passwords and other text entered there.
In February 2020 the US Defense Information Systems Agency (DISA) announced it had suffered a data breach exposing the personal information of 8,000 civilian and military personnel working for a combat support agency of the DoD. DISA is responsibility for supporting secure White House communications, including those of the President. In addition it also establishes and supports communications networks in combat zones and takes care of military cyber-security issues, as such might have exposed data affecting as many as 200,000 users.
In March 2020 it was announced that North Korean hackers targeted individuals involved with North Korean refugees. Active since at least 2012 and also referred to as APT37, Group123, and Temp.Reaper, ScarCruft is likely backed by the North Korean government and is known for the targeting of defectors, journalists, and government organisations, among others. Following infection with PowerShell malware, the adversary spied on the victim for months, and even attempted to spear-phish victims’ associates. The security firm discovered that the adversary used stolen Facebook credentials to contact a victim’s acquaintance, after which a phishing email was sent from a stolen account to the potential victim. A password-protected RAR archive containing a malicious Word document was attached to the message. Malicious macros in the document were designed to run shellcode and fetch the next stage payload. The computer of the person who sent the phishing email was found to be infected with a PowerShell script functioning as a backdoor. The new package, called Chinotto, provided attackers with control over the compromised machines, as well as with data exfiltration capabilities. It could download and upload files, remove files, archive directories and exfiltrate them, take screenshots, and run Windows commands, among others. The Android version of Chinotto asks for various permissions that allow it to collect sensitive information such as contacts, messages, call logs, device data, and audio recordings. The malware is likely to have been deployed via smishing (SMS phishing) attacks. Naturally in the same month South Korean hackers were found to have used five previously unreported software vulnerabilities to conduct a wide-ranging espionage campaign against North Korean targets.
Also in March 2020 it was revealed that Saudi mobile operators exploited a flaw in global telecommunications infrastructure to track the location of Saudis traveling abroad. The kingdom has used mobile spyware to hack into the phones of dissidents and activists and it would appear that they collected location tracking by exploiting weaknesses in Signalling System 7 (SS7), a set of protocols to route and direct calls and messages between networks. It’s the reason why a customer of one carrier can call a phone of another carrier, even when they’re in another country. But experts say that weaknesses in the system have allowed attackers with access to the carriers (mostly governments) to listen in to calls and read text messages. SS7 also allows carriers to track the location of devices to just less than 100 m in densely populated cities by making a "provide subscriber information" (PSI) request. These PSI requests are typically to ensure that the cell user is being billed correctly, e.g. when they are roaming on a carrier in another country. Requests made in bulk and excess can indicate location tracking surveillance. This is not a new problem but it is not clear how to find a solution that does not block legitimate carrier requests. End-to-end encrypted apps, like Signal and WhatsApp, have made it harder for spies to snoop on calls and messages. But it’s not a panacea. As long as SS7 remains a fixture underpinning the very core of every cell network, tracking location data will remain fair game.
In April 2020 US officials reported seeing a surge of attacks by the Chinese military and other Chinese hackers against healthcare providers, pharmaceutical manufacturers, and the US Department of Health and Human services amidst the COVID-19 pandemic. The US government issued a stark and unusual warning asserting that China's efforts to hack health care and pharmaceutical companies posed a "significant threat" to the nation's response to the coronavirus pandemic. It was stated that "These actors have been observed attempting to identify and illicitly obtain valuable intellectual property (IP) and public health data related to vaccines, treatments, and testing from networks and personnel affiliated with COVID-19-related research". One tactic cyber attackers are now using against health care institutions is known as "password spraying", a single common word is tested for many users on one network, in the hope that at least one account will be penetrated.
In May 2020 the NSA announced that Russian hackers associated with the GRU had been exploiting a bug that could allow them to take remote control of US servers, at the same time it was also announced the German officials found that a Russian hacking group associated with the FSB had compromised the networks of energy, water, and power companies in Germany by compromising the firms’ suppliers. GRU is Russia's military intelligence agency and they play an important role in foreign and national security issues, both tactical and strategic. They conduct extensive cyber, disinformation, propaganda and assassination and sabotage missions, etc. The FSB is responsible for domestic counterintelligence, and acts also in neighbouring post-Soviet states, i.e. it is primarily responsible for domestic security. The FSB has recruited cyber specialists from the criminal community, whereas GRU, with its signal intelligence responsibilities, has developed in-house capabilities (a simplification but useful).
In June 2020 the Lookout Threat Intelligence team discovered four Android surveillanceware tools, which they named SilkBean, DoubleAgent, CarbonSteal, and GoldenEagle. These four interconnected malware tools are elements of much larger mAPT (mobile advanced persistent threat) campaigns originating in China, and primarily targeting the Uyghur ethnic minority, says the team. Activity of these surveillance campaigns has been observed as far back as 2013. The main goal of these apps is to "gather and exfiltrate personal user data to attacker-operated command-and-control servers, and each malware tool has its own unique data gathering priorities and techniques". Many samples of these malware tools were trojanised legitimate apps (i.e. the malware maintained complete functionality of the applications they were impersonating in addition to its hidden malicious capabilities). Lookout found evidence that the malware predominantly targeted Uyghurs, but also, to a lesser extent, Tibetans. These two groups are reportedly the main focus of China’s “counter-terrorism” activity. Titles and in-app functionality of samples, such as “Sarkuy” (Uyghur music service), “TIBBIYJAWHAR” (Uyghur pharmaceutical app) and “Tawarim” (Uyghur e-commerce site) show that the majority of this activity focused on Uyghurs. They reported that the Chinese government’s "Strike Hard Campaign against Violent Terrorism", which launched in mid-2014, led to the creation of the National Security Strategic Guidelines, the National Security Law and the Counterterrorism Law in 2015. The report mentions that the past activity of this mAPT is connected to previously reported desktop APT activity in China4, which is linked to GREF, a China-based threat actor also known as APT15, Ke3chang, Mirage, Vixen Panda and Playful Dragon". In addition, they noticed that campaigns by this mAPT are also active outside of China, based on the languages and services targeted by the malware samples. They found that at least 14 different countries may have be affected by the campaigns. Twelve of these are on the Chinese government’s official list of "26 Sensitive Countries" which according to public reporting, are used by authorities as targets. There are at least four other Android tools in the same mAPT actor’s mobile surveillance arsenal. They are publicly known as HenBox6, PluginPhantom7, Spywaller8, and DarthPusher9, which have been previously observed targeting Chinese-speaking individuals and those of the Uyghur ethnic minority. The surveillance apps of these campaigns were likely distributed through a combination of targeted phishing and fake third-party app stores. Check out this report on what is happening in the Xinjiang Uyghur Autonomous Region (XUAR).
In July 2020 Chinese state-sponsored hackers broke into the networks of the Vatican to conduct espionage in the lead-up to negotiations about control over the appointment of bishops and the status of churches in China. The Vatican and Beijing were expected to engage in talks this year over the renewal of a landmark 2018 deal that stabilised relations between China and the Church. It would appear that the attacks targeted the Vatican and the Catholic diocese of Hong Kong, including the head of the Hong Kong Study Mission, who is seen as Pope Francis’ de facto representative to China.
Also in July 2020 Canada, the UK, and the U.S. announced that hackers associated with Russian intelligence had attempted to steal information related to COVID-19 vaccine development. The hackers, who belong to a unit known variously as APT29, "the Dukes" or "Cozy Bear" are targeting vaccine research and development organisations in the three countries, the officials said in a joint statement. The unit is one of the two Russian spy groups that penetrated the Democratic Party's computers in the lead-up to the 2016 presidential election. The FBI also said that "it’s not unusual" to see "cyber activity" traced to China soon after a pharmaceutical company or research institution makes an announcement about promising vaccine research, "it’s sometimes almost the next day".
In August 2020 US officials announced that North Korean government hackers are tapping into banks around the globe to make fraudulent money transfers and cause ATMs to spit out cash. U.S. law enforcement titled the hacking campaign "Fast Cash" and blamed North Korea’s Reconnaissance General Bureau, a spy agency, for it. They described the operation as going on since at least 2016 but ramping up in sophistication and volume recently.
Also in August 2020 it was announced that seven semiconductor vendors in Taiwan were the victim of a two-year espionage campaign by suspected Chinese state hackers targeting firms’ source code, software development kits, and chip designs. The series of deep intrusions, called Operation Skeleton Key due to the attackers' use of a "skeleton key injector" technique, appeared aimed at stealing as much intellectual property as possible. This group of hackers had been called "Chimera", but there is evidence that ties them to mainland China and loosely links them to the notorious Chinese state-sponsored hacker group Winnti, also sometimes known as Barium, or Axiom.
In October 2020 a spokesperson for China’s Foreign Ministry responded to accusations that Chinese state-sponsored hackers were targeting the US defence industrial base by declaring that the United States was an "empire of hacking", citing 2013 leaks about the NSA’s Prism program. A little more than a year ago, China had almost no diplomatic presence on Twitter. A handful of accounts, many representing far-flung diplomatic outposts, operated without apparent coordination or direction from Beijing. Today, the work of Chinese diplomats on Twitter looks very different. More than 170 of them bicker with Western powers, promote conspiracies about the coronavirus, and troll Americans on issues of race. The quadrupling in the past year and a half of China’s diplomatic presence on a site blocked within China suggests that turning to Western platforms to influence the information environment beyond China’s borders is no longer an afterthought but a priority. In pursuing increasingly assertive tactics to shape how China is perceived online, Beijing has borrowed elements of Russia’s playbook. China’s "wolf warrior" diplomats, a phrase that comes from a jingoistic Chinese film franchise and refers to a new approach among the Chinese diplomatic corps to more aggressively defend their home country online, propagate conflicting conspiracy theories about the origins of the novel coronavirus that are designed to sow chaos and deflect blame. It is using these so-called warriors, together with its sprawling state media apparatus and, at times, covert trolling campaigns, to amplify false theories on social media and in the news. And it is doing all this by leaning on the propaganda outlets run by Moscow, Caracas, and to a lesser extent, Tehran, and the network of contrarian agitators they leverage to promote anti-Western content. Beijing has deployed hashtag campaigns and dedicated social media accounts to flood conversations about its human rights record with positive content.
Also in October 2020 India's National Cyber Security Coordinator announced that cyber crimes in India cost almost $17 billion in 2019.
Also in October 2020 the US Department of Homeland Security revealed that hackers targeted the US Census Bureau in a possible attempt to collect bulk data, alter registration information, or compromise census infrastructure. The data compiled by the Bureau is used by the federal government to assign over $675 billion in federal funds to local, tribal, and state governments every year. Warning had already been issued concerning state-affiliated actors linked to China, Iran, Russia and North Korea that might attempt to compromise or disrupt critical 2020 elections, as well as try to impact the US voter’s opinions and preferences.
In November 2020 a Mexican facility owned by Foxconn was hit by a ransomware attack that the hackers claim resulted in 1,200 servers being encrypted, 20-30 TB of backups being deleted, and 100 GB of encrypted files being stolen. It started with DoppelPaymer ransomware published files belonging to Foxconn on their ransomware data leak site. The leaked data includes generic business documents and reports but does not contain any financial information or employee's personal details. Attackers demanded $34 million ransom in bitcoins. What they did was to encrypt about 1,200 servers, stole 100 GB of unencrypted files, and deleted 20-30 TB of backups. Give that the data was published, I guess Foxconn did not pay the ransom. Other victims attacked by DoppelPaymer in the past include Compal, PEMEX (Petróleos Mexicanos), the City of Torrance in California, Newcastle University, Hall County in Georgia, Banijay Group SAS, and Bretagne Télécom.
In December 2020 over 200 organisations around the world, including multiple US government agencies, were revealed to have been breached by Russian hackers who compromised the software provider SolarWinds and exploited their access to monitor internal operations and exfiltrate data. Here is the story, but what the advanced persistent threat (APT) actors did was infiltrate the supply chain of SolarWinds, inserting a backdoor into the product. This was particularly damaging since SolarWinds was a developer of an IT monitoring and management tool called Orion, used by more than 33,000 organisations and companies around the world. As customers downloaded the Trojan Horse installation packages from SolarWinds, attackers were able to access the systems running the SolarWinds product(s).
Key Computer Security Topics in 2019
In 2019 the most important trend was probably the continued escalation of web attacks, driven in part by new vulnerabilities found in common applications. Application-specific and web-application attacks accounted for over 32% of all hostile traffic. One study found more than 2,000 new vulnerabilities for 105 commonly used applications. Google Android remained by far the most vulnerable, followed by Adobe Acrobat and Flash (Google Chrome also remained the most vulnerable browser). In fact more than 40% of application vulnerabilities were considered high-risk or critical (meaning total loss of system protection). For example, AndroRAT (available on GitHub) allows hackers to access contacts, call logs and location, and they can also open the browser, stream videos, take pictures, stream sound from the microphone, send text messages, and place a call. FaceNiff hacks the accounts of Android users' social media sites. Not to be outdone, iRET and iSPY are tools for hacking iOS devices. And we should not forget that open-source applications, because of the sheer number of applications, are also a rich target for hackers. In Sept. 2019 it was reported that 13 small office/home office (SOHO) routers and network-attached storage (NAS) devices were tested and 125 critical vulnerabilities were found.
2019 has seen an increased effort to replace passwords with fingerprint, facial identification and speaker recognition being included in a multi-factor authentication model. Banks are increasingly using advanced authentication technologies in their sales literature to attract new customers. Phishing remains the bread and butter of the hacker, and more than ⅔ of all incidents still involve phishing. 'Smishing' (SMS texting attacks) exploiting social media platform data, and 'vishing', or phone calls with a live person (e.g. the Microsoft virus control centre), also remain popular and remarkable effective. A related develop is the idea to bake authentication into a user's hardware (e.g. Intel's Skylake chips).
In a recent intelligence report they noted that fraud rates are skyrocketing in the US in 2019. One report mentioned that there are 90 voice channel attacks occurring every minute in the US. Fraud calls concern insurance, retail, banking, card issuers, brokerages, credit unions, etc. The fraud rate is now 1 call in every 685 calls. Insurance voice fraud has increased by nearly 250% for claims over $500,000. Synthetic voices and augmented images with video and sound are now being used.
Fortinet, a US provider of cybersecurity software and services, registers 500,000 attacks every minute. Every day around 230,000 malware samples are created by hackers. Attacks on mobile messaging and social media have increased by more than 200% in just one year. Mobile botnets emerged as a major threat and the number of mobile malware variants tripled from 2018 to 2019. One report noted that 70% of all fraudulent transactions originated from a mobile phone, and this type of fraud has increased by nearly 700% since 2015.
Globally financial service companies saw the most attacks (17%) with nearly half (42%) of the attacks coming from the US. Technology companies were also major targets (17%), and 37% of those attacks came from China. There are significant regional variations, e.g. 30% of all attacks in Europe, Middle East and Africa are on financial service companies, whereas technology companies are the main targets in Asia. Incredibly, results reported in 2016 continue to be the norm, with nearly 30% of people opening phishing emails, and 12% of them clicking on the links or opening attached files. There are now phishing apps that automatically create effective and unique messages to send to victims, so this problem is not likely to go away any time soon.
You can now hire a botnet, and it can cost as little as $50 to bring down a website. One report claimed that cyber attacks are the primary reason for around 60% of small companies going out of business. The cost of a successful cyber attack is now estimated at about $5 million, or about $300 per employee (more than 40% of that is attributed to data loss). Destructive attacks are on the increase, as is the ability of the attacker to avoid identification.
Some attackers have shifted their interests from ransomware to cryptomining, with coin mining now moving from web-based to host mining. One commonly reported source of coin mining is the so-called 'dorm room mining' with students generating cryptocurrency which they later exchange for cash. Illicit coin mining has been identified with Rocke, a Chinese crimeware group active also in ransomware, 8220 Mining Group, also active in China, and the Tor2Mine group. Coin mining is profitable and has a low entry barrier. Some existing malware tools have had coin mining added. Once installed on a host coin mining is difficult to detect. Attackers try to exploit the graphics processor units (GPU) which are very efficient in processing the mathematical computations required for coin mining. A classical way to detect illicit coin mining was to monitor CPU/GPU usage, but the latest systems can 'throttle back' by measuring usage and keeping it at about 80%. CoinHive is an alternative, in that it is 'drive-by' mining using the browser to mine as long as the page is open.
This does not mean that ransomware dropped off the radar screen, e.g. in the US ransomware attacks on school districts rose substantially (attacks on consumers have gone down). If anything ransomware has become more visible in 2019 due to the increase in attacks on schools. It has been estimated that about 4,000 ransomware attacks occur daily, mostly exploiting infected attachments delivered in personalised emails, or so-called 'spear phishing'. It has been estimated that in the US about 75% of all organisations received targeted phishing attacks in the period 2018-2019. Local government remains the firm favourite but healthcare organisations have been pushed back into third. The number of attacks on local government remains modest, but they pay on average 10 times as much as their private-sector counterparts. In a review, US schools were found to be using 250 unique OS versions and more that 137,000 unique application versions. In addition (in the US) more than 40% of students use web proxy and VPN applications, which are particularly vulnerable to rogue applications. Attacks against business are on the rise, but so is businesses ability to detect ransomware attacks.
Another major trend seen in 2019 is the number of data records exposed in data breaches (⅓ in the US alone). In 2019 there was an increase of 112% in total records exposed, representing 7.9 billion records only for the January to September. And this does not count the data breaches not made public. Along with this increase in data breaches there has been an increased interest in holding data in an encrypted form.
Reading through the reports, etc. everyone is writing about both hackers and computer security companies using 'artificial intelligence'. However there is little or no detail about what this means. The best I can see is that companies are trying to use automated and intelligent system to rapidly detect attacks. Another area of interest is in having intelligent systems that keep track of all the hardware and software assets in an organisation, so that certification, renewals, installations, revocations, etc. are maintained up-to-date. A third area of interest is performing vulnerability assessments. A longer-term interest is in using intelligent systems to detect anomalous user behaviour.
Another problem is a skills shortage, coupled with a lack of bespoke training programs. This skill shortage includes a lack of expertise in handling proprietary and customer data. Around 65% of all businesses state that they don't have any specialist in-house expertise in computer security. Yet at the same time more than 70% of consumers state that they are more concerned about retailers misusing their personal information than information being taken by hackers.
State sponsored attacks have become increasingly commonplace. Below we have a short selection of some of the most important attacks made in 2019:-
The year 2018 closed with the revelation that North Korean hackers had targeted the Chilean interbank network after tricking an employee into installing malware during a fake job interview. It was also reported that North Korean hackers had also stole the personal information of almost 1,000 North Korean defectors living in South Korea. Chinese hackers were found to have compromised the EU’s communications systems, maintaining access to sensitive diplomatic cables over several years. The United States, in coordination with Australia, Canada, the UK, and New Zealand, accused China for conducting a 12-year campaign of cyber espionage targeting the IP and trade secrets of companies across 12 countries. Specifically the US Navy reported that Chinese hackers had repeatedly stolen information from Navy contractors including ship maintenance data and missile plans. Security researchers discover a cyber campaign carried out by a Russia-linked group targeting the government agencies of Ukraine as well as multiple NATO members, and the Ukraine security services blocked an attempt by the Russian special services to disrupt the information systems of Ukraine’s judicial authority. The Czech security service announced that Russian intelligence services were discovered to have been behind attacks against the Czech foreign ministry in 2017. And finally it was confirmed that Chinese hackers breached the systems of an American hotel chain, stealing the personal information of over 500 million customers.
January 2019 started with the US Department of Justice announcing an operation to disrupt a North Korean botnet that had been used to target companies in the media, aerospace, financial, and critical infrastructure sectors. US prosecutors then issued two indictments against Huawei and its CFO Meng Wanzhou alleging crimes ranging from wire and bank fraud to obstruction of justice and conspiracy to steal trade secrets. Security researchers revealed that Iranian hackers have been targeting the telecom and travel industries since at least 2014 in an attempt to surveil and collect the personal information of individuals in the US, Middle East, Europe, and Australia. The US Securities and Exchange Commission charged a group of hackers from the US, Russia, and Ukraine with a breach of their online corporate filing portal used to execute trades based on non-public information. And hackers released the personal details, private communications, and financial information of hundreds of German politicians, with targets representing every political party except the far-right AfD.
In February 2019 the UN International Civil Aviation Organisations revealed that in late 2016 it was compromised by China-linked hackers who used their access to spread malware to foreign government websites. Hackers associated with the Russian intelligence services had targeted more than 100 individuals in civil society groups working on election security and democracy promotion. The European aerospace company Airbus reveals it was targeted by Chinese hackers who stole the personal and IT identification information of some of its employees, and the Norwegian software firm Visma revealed that it had been targeted by hackers from the Chinese Ministry of State Security who were attempting to steal trade secrets from the firm’s clients.
In March 2019 an Iranian cyber espionage group targeted government and industry digital infrastructure in Saudi Arabia and the US, and it was confirmed that Iran's intelligence service had hacked into former IDF Chief and Israeli opposition leader Benny Gantz’ cellphone ahead of Israel’s April elections. Iranian hackers went on to target thousands of people at more than 200 oil-and-gas and heavy machinery companies across the world, stealing corporate secrets and wiping data from computers. The UN Security Council reported that North Korea has used state-sponsored hacking to evade international sanctions, stealing $670 million in foreign currency and cryptocurrency between 2015 and 2018. Following an attack of Indian military forces in Kashmir, Pakistani hackers targeted almost 100 Indian government websites and critical systems.
April 2019 saw Amnesty International’s Hong Kong office announced it had been the victim of an attack by Chinese hackers who accessed the personal information of the office’s supporters. Hackers also used spoofed email addresses to conduct a disinformation campaign in Lithuania to discredit the Defence Minister by spreading rumours of corruption, and at the same time the Finnish police probed a denial of service attack against the web service used to publish the vote tallies from Finland’s elections.
In May 2019 it was announced that hackers affiliated with the Chinese intelligence service reportedly had been using NSA hacking tools since 2016, more than a year before those tools were publicly leaked. The Israeli Defence Forces launched an airstrike on the Hamas after they unsuccessfully attempted to hack Israeli targets.
In June 2019 it was discovered that over the course of seven years, a Chinese espionage group had hacked into ten international cellphone providers operating across thirty countries to track dissidents, officials, and suspected spies. China also conducted a denial of service attack on encrypted messaging service Telegram in order to disrupt communications among Hong Kong protestors. US grid regulator NERC issued a warning that a major hacking group with suspected Russian ties was conducting reconnaissance into the networks of electrical utilities. And at the same time US officials revealed their ongoing efforts to deploy hacking tools against Russian grid systems as a deterrent and warning to Russia. Late we would see that state-sponsored Chinese hackers conducted a spear-phishing campaign against employees of three major US utility companies.
In July 2019 several major German industrial firms including BASF, Siemens, and Henkel announced that they had been the victim of a state-sponsored hacking campaign reported to be linked to the Chinese government. And a Chinese hacking group was discovered to have targeted government agencies across East Asia involved in information technology, foreign affairs, and economic development. Microsoft revealed that it had detected almost 800 cyberattacks over the past year targeting think tanks, NGOs, and other political organisations around the world, with the majority of attacks originating in Iran, North Korean, and Russia.
In August 2019 China was found to have used compromised websites to distribute malware to Uyghur populations using previously undisclosed exploits for Apple, Google, and Windows phones. A previously unidentified Chinese espionage group was found to have worked since 2012 to gather data from foreign firms in industries identified as strategic priorities by the Chinese government, including telecommunications, healthcare, semiconductor manufacturing, and machine learning. The group was also active in the theft of virtual currencies and the monitoring of dissidents in Hong Kong. A suspected Indian cyber espionage group conducted a phishing campaign targeting Chinese government agencies and state-owned enterprises for information related to economic trade, defence issues, and foreign relations.
Updating this webpage in Nov. 2019 means that much of what happened in September though to November has not yet been released in the public domain. A blog at IT Governance does a decent job in listing data breaches and cyber attacks month by month.
Also in August 2019 the problem of embedded microprocessors was revisited (the 2020 market for these embedded devices in estimated to rise to above $200 billion). Experts have suggested that every embedded microprocessor tested can be compromised in some way (see report on vulnerability of Cisco switches, routers, and firewalls). Also there were a number of demonstrations where experts claimed that they could hack into any company IP phone system so as to listen to everything being said.
In September 2019 the US voting machines again came under scrutiny, with hackers trying to find a way to remotely control them. The techniques could not be exploited during an election, but the weaknesses could undermine confidence in the entire electoral system. In particular the ballot-marking devices used by those with physical impairments or language barriers are more than 15 years old, and are considered extremely unreliable and having virtually no 'cyber' protection. In addition about 20% of the voting machines used leave no paper trail that could be audited (and some of the machines are more than 20 years old).
However in October 2019 it was reported that Iran had started its cyber attack of Donald Trump's re-election campaign. And not to be outdone, in November 2019 the UK Labour Party suffered a large-scale cyber attack on it's election campaign data and website. In fact New Zealand announced that about ⅓ of all attacks were state sponsored, and the trend in 2019 was for attacks that evaded detection for longer periods and as a consequence had a greater impact. You may think that China will want to refute all accusations concerning state hacking, but on 16-17 November they hosted the Tianfu Cup, where their best hackers tested zero-day hacks against some of the world's most popular apps.
Naturally for-profit hacking has also progressed in 2019. For example the Pipka JavaScript Skimmer is now able to erase itself from HTML code after execution. It collects data such as payment account numbers, cardholder name and address, expiration date, and even the CVV. Now that WannaCry is in the past, we have a new ransomware vulnerability called BlueKeep, which apparently also tries to install cryptomining software (as mentioned earlier). Also it does not help that Facebook has apparently been activating iPhone owners' cameras while they scrolling through their news feeds (Facebook says it's a bug). And WhatsApp, another app in the Facebook stable, continues to have problems and is now accused of quietly patching another critical vulnerability in its app that could have allowed attackers to remotely compromise targeted devices. And it's not just Facebook, because a misconfigured Amazon 'Simple Storage Service' (S3) exposed 93 million billing files on patients of three US drug and alcohol addiction facilities. Still Facebook did announce that between April and September 2019 they removed 3.2 billion fake accounts. Of course you can also 'steal' data legally, for example Google has collected patient data from 2,600 US health facilities without informing doctors or patients.
Key Computer Security Topics in 2018
In 2018 Cyber crime was the 2nd most reported type of crime in the world, and in the UK it represented more than 50% of all reported crime. Attackers reside within a network for an average of 146 days before being detected. Usually attackers enter using compromised usernames and passwords. Again in the UK, 70% of all financial fraud was through remote purchases using stolen personal and credit card data. One estimate put credit card fraud worldwide at $190 billion a year.
Identity theft is, and will remain, a major problem. In the U.S. for 2017 more social security numbers were stolen than credit card numbers, and the amount stolen through complex identity fraud was estimated at nearly $17 billion. With the introduction of chip cards, criminals shifted their focus to new account fraud, i.e. opening a new bank or credit card account with the victims name (the amount stolen per account was on average $450). In the U.S. nearly 17 million people were victims of identity fraud. However tax-related fraud and credit card fraud still remained the most important. Check out this guide to find out what to do to protect yourself against identity theft.
So-called data breaches sounds very technical, but it hides a simple reality. It's your and my email addresses (and occasionally more sensitive personal data) that are 'lost' or stolen. With this brilliant visualisation we can see just how big the problem has become, the following breaches occurred in 2018, 6 million user accounts on Instagram, 37 million customer records with Panera Bread, 150 million user accounts with passwords from MyFitnessPal, 143 million accounts from Equifax, and 412 million users accounts with passwords for Friend Finder Network.
In 2018 ransomware became a $1 billion industry, and we tend to forget that financial trojans were some of the first pieces of malware to be monetised, and they still account for more losses than ransomware. This is just one part of a kind of shadow economy that has emerged where data can be bought and sold on the Dark Web and large botnets, ransomware-as-a-service and DDoS-as-a-service are available for rent or as franchises.
Two new problems, entitled Spectre and Meltdown, were detected as flaws in microprocessors. Firstly they are flaws, and secondly they have not been any exploits of the flaws so far. Thirdly they are hardware flaws and therefore can't be fixed by the usual software patches. This could be the start of a new trend where hackers start to focus more on firmware and hardware, who knows.
Key Computer Security Topics in 2017
2017 was certainly characterised by 1,000's of computer being infected simply because users had not updated to the latest operating systems, nor had they kept up-to-date with security patches. More than 1.3 million computers running Windows were infected with the WannaCry ransomware despite Microsoft having issued a security update more than a month before the exploit was leaked.
Even if you followed all the rules there were still potential problems. For example CCleaner, a popular Windows utility, was found to include malware designed to steal personal data from infected machines. And there was a specific version just to attack Cisco, Sony and HTC. This was followed by the revelation that some HP laptops had a key logger hidden in the audio driver. The driver was supposed to alert when a particular key was hit, but the driver was actually capturing all the keystrokes, i.e. passwords, user names, etc. And then we learned that there was a backdoor in WhatsApp's end-to-end encryption. Two notable 'academic' developments were the announcement that encrypted data transiting a Wi-Fi network could be read (under quite strict pre-conditions) using the Krack exploit, and that printers could be used to launch malware attacks. On a more practical level US voting machines were breached in under 90 minutes by experts in a competition in Las Vegas. Apple discovered a security flaw that granted admin access on High Sierra without needing the password. And to close the year experts found that it was possible to connect with Bluetooth devices without user permission or even pairing the devices.
Ransomware, phishing and data breaches remained major problems. There were more than 5,000 publicly acknowledged data breaches in 2017 exposing more than 7.8 billion records. But black market prices have dropped for personal and financial data, so the focus moved to medical insurance records. A study in 2016 found that there had already been more than 1,500 data breaches involving medical data. It has been estimated that cyber attacks will cost U.S. hospitals more than $300 billion over the next 5 years, and that 1 in every 13 patients will have their data compromised.
Key Computer Security Topics in 2016
In 2016 ransomware was a major concern, with more than 600 million attacks on large and small businesses. The average ransom demand was between $600 and $700, and even the FBI suggested that it was easier to pay that to try to fight it. The year saw a variety of new ransomware strains appear. Ransomware usually was spread via phishing scams and exploit kit attacks, but self-propagating cryptoworms have now appeared. Jigsaw was a new strain offering it victims only 24 hours to pay the $150 ransom fee. After the deadline it started to delete files every hour, and increasing hour upon hour. It deleted all the remaining files if the ransom was not paid within 72 hours. This type of ransomware was particularly sadistic since most varieties only encrypt the files to make them inaccessible, so there is always a chance that decryption keys will become available at a later date.
A new business model for ransomware appeared, namely affiliate programs where the profits are shared between the affiliate and the ransomware developer. The ransomware Chimera actually invited its victims to join their affiliate program. Cerber is known to have netted the author nearly $1 million per year independently of their own attack campaigns. The key here is the threat will grow bigger and faster because the user base is no longer limited to the developer.
In Jan. 2016 there was an article on traffic-cash.xyz, a referrer spam (or 'ghost spamming'). Many websites use Google Analytics. This scam mixes data into the Google Analytics account for that website. It then appears that someone has visited the website from traffic-cash.xyz, however this is not the case. This is just one type of referrer spam URL’s. They offer a new way to monetise the website, but in fact they want to collect personal data, and sign the website up to propellerads.com, a referrer spam URL. This kind of data can ruin a website’s analytical data, by mixing in useless data on audience, acquisitions, user behaviour, etc. In addition they use referrer spam to promote their own website, and to boost their own rank on Google search results (by creating backlinks). This is done by logging requests into the website’s access log, which is then crawled by Google’s indexing bots.
Through 2016 there was a major increase in phishing attacks on Gmail accounts. The user received an email sent to their Gmail account. The email often came from someone they knew who's account had already been hacked. It also often included something that looks like an image of an attachment they recognised from the sender. Clicking on the image, they expecting Gmail to give them a preview of the attachment. Instead, a new tab opened up with a cloned password text box, and they were prompted to sign in again. People would glance at the location bar and see 'accounts.google.com' in there somewhere. So they signed in on what looked like a functional sign-in page. Once they have completed the fake sign-in, their account was compromised. The attackers could then log in to the account and use one of the persons actual attachments, along with one of their actual subject lines, and then sends it to people in the contact list. And so the attacked was propagated.
Dictionaries and Jargon
Wikipedia has a Jargon File which tries to follow how slang usage, etc. evolved from 1975 through to 2003
“The Original Hacker’s Dictionary” (dates from around 1988) and “The Jargon File” (dates from 1991), and “The New Hacker’s Dictionary” is from 2002
The Motherboard e-Glossary of Cyber Terms and Hacking Lingo (dates from 2016)
The Hacker Dictionary looks up-to-date
And there is Hackterms, a crowdsourced dictionary of coding terms.
There are a number of 'official' sources that try to maintain an up-to-date list of terms, expressions, etc.
The US National Institute of Standards and Technology hosts the Computer Security Resource Center which has an online glossary of computer security terms. In the UK the National Cyber Security Centre also has on online glossary. There are several publications of terminology, abbreviations and acronyms, the most notable being the "Glossary of Key Information Security Terms" from NIST and "A Dictionary of Information Security Terms, Abbreviations and Acronyms" from IT Governance UK.
Warning - people need to change what they are checking in the location bar
Everyone say's “Check the location bar in your browser to make sure you are on the correct website before signing in. That will avoid phishing attacks that steal your username and password". Often people see that there is something like ‘accounts.google.com‘ in the location bar, so it must be good. Not true!
This phishing technique uses something called a ‘data URI’ to include a complete file in the browser location bar. A quick look at the browser location bar sees ‘data:text/html…..’ as part of a very long string of text. If you widen out the location bar it looks like this:
There is a lot of whitespace, but on the far right there is the beginning of what is a very large chunk of text. This is actually a file that opens in a new tab and creates a completely functional fake Gmail login page which is designed to collect user credentials and send them to the attacker.
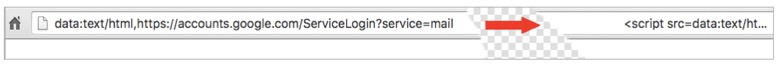
On the far left of the browser location bar, instead of ‘https’ we see ‘data:text/html’, followed by the usual ‘https://accounts.google.com….’. People do not pay close attention and ignore the ‘data:text/html’ preamble, assuming the URL is safe.
When signing in to any service, check the browser location bar and verify the protocol, then verify the hostname. It should look something like this:

Make sure there is nothing before the hostname ‘accounts.google.com’ other than ‘https://’ and the 'padlock' symbol. Take special note of the green colour and 'padlock' symbol that appears on the left. If you can’t verify the protocol and verify the hostname, stop and think about what you just clicked on to get to that sign-in page.
If in doubt use virustotal (an excellent free Google service) to analyses suspicious files and URL’s.
People should also enable two-factor authentication if it is available. Here is the full article. Just run a Google search on “how to cash in on phishing”, and you will get a long list of the latest type of attacks.
A study on malware statistics for 2013-2015 indicated that 431 million new malware variants were added to the pre-existing pool of malware strains. Check out this 2017 article for more information.
This article looks at malware that targets ATM’s. This White Paper looks at attacks aimed at the travel and entertainment sector, i.e. spoofing client devices or identities. But don’t forget that even today people are still being scammed by fake anti-virus offers.
Messages telling you to install and update security software for your computer seem to be everywhere. So you might be tempted by an offer of a “free security scan,” especially when faced with a pop-up, an email, or an ad that claims “malicious software” has already been found on your machine.
Avoid at all costs, this type of message is a come-on for a rip-off.
News, Threat Detection and Response
Cyber Threat Source Descriptions and Alerts from US-CERT
NIST has a Computer Security Resource Center
CCDCOE is the NATO Cooperative Cyber Defence Centre of Excellence in Tallinn, Estonia
virustotal is an excellent free Google service that analyses suspicious files and URL’s
Microsoft has a Threat Research & Response Blog on their 'Microsoft Secure', and they also have a Safety & Security Center
Securelist is run by Kaspersky Lab., as is Threat Post and the Targeted Cyberattacks Logbook
Hacking Threat is a commercial online source of security news
FireEye has a useful set of resources including blogs and even some free software
Krebs on Security is a reputable blog by an ex-Washington Post journalist
Recorded Future is a commercial security company that also provides a blog, a free daily newsletter, and other resources
Security Week is a free information magazine covering malware, cybercrime, etc.
DarkReading is an information resource covering everything from breaches to analytics
InfoRisk Today has a resource centre covering things such as ransomware and GDPR
Symantec is a well known provider of security tools
HackRead is an information resources for topics such a cyber crime and privacy
WeLiveSecurity provides news, views and insights to the security community
Digital Shadows had a blog and some White Papers
SentinelOne has a resource page with White Papers, Case Studies, Videos & Demos, Reports, eGuides, etc.
malpedia is a resource for rapid identification and actionable context when investigating malware
Mitre ATT&CK is a knowledge base of adversary tactics and techniques based on real-world observations
Heimdal Security has a whole range of guides and links to topics ranging from concepts through to tools and threats.
And if you need to start to think about computer security, why not take the Network and Information Security Quiz.
If you thought you knew it all, think again...